Once the individuals have attained a consensus, transactions to the blockchain are created into blocks such as the web pages of a ledger reserve. Combined with the transactions, a cryptographic hash can also be appended to the new block.Cyber hackers try to look for very hot wallets and may try to steal Those people holdings. copyright wallets will
 Amanda Bynes Then & Now!
Amanda Bynes Then & Now!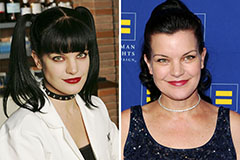 Pauley Perrette Then & Now!
Pauley Perrette Then & Now!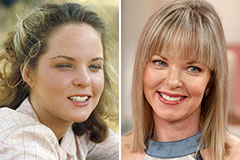 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Tonya Harding Then & Now!
Tonya Harding Then & Now! Dolly Parton Then & Now!
Dolly Parton Then & Now!